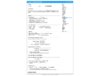
Wed Feb 1 02:02:53 2012 us=755706 OpenVPN 2.2.1 mipsel-linux [SSL] [LZO2] [MH] [PF_INET6] [IPv6 payload 20110424-2 (2.2RC2)] built on Jan 17 2012
Wed Feb 1 02:02:53 2012 us=757918 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Wed Feb 1 02:02:54 2012 us=490432 Diffie-Hellman initialized with 2048 bit key
Wed Feb 1 02:02:54 2012 us=494377 WARNING: file '/tmp/flash/openvpn/box.key' is group or others accessible
Wed Feb 1 02:02:54 2012 us=503083 Control Channel Authentication: using '/tmp/flash/openvpn/static.key' as a OpenVPN static key file
Wed Feb 1 02:02:54 2012 us=503577 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 1 02:02:54 2012 us=504000 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 1 02:02:54 2012 us=504504 TLS-Auth MTU parms [ L:1590 D:166 EF:66 EB:0 ET:0 EL:0 ]
Wed Feb 1 02:02:54 2012 us=505047 Socket Buffers: R=[108544->131072] S=[108544->131072]
Wed Feb 1 02:02:54 2012 us=506290 WARNING: potential TUN/TAP adapter subnet conflict between local LAN [192.168.2.0/255.255.255.0] and remote VPN [192.168.2.0/255.255.255.0]
Wed Feb 1 02:02:54 2012 us=508064 OpenVPN ROUTE: OpenVPN needs a gateway parameter for a --route option and no default was specified by either --route-gateway or --ifconfig options
Wed Feb 1 02:02:54 2012 us=508441 OpenVPN ROUTE: failed to parse/resolve route for host/network: 192.168.2.0
Wed Feb 1 02:02:54 2012 us=527951 TUN/TAP device tap0 opened
Wed Feb 1 02:02:54 2012 us=528434 TUN/TAP TX queue length set to 100
Wed Feb 1 02:02:54 2012 us=528886 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Wed Feb 1 02:02:54 2012 us=529479 /sbin/ifconfig tap0 192.168.2.100 netmask 255.255.255.0 mtu 1500 broadcast 192.168.2.255
Wed Feb 1 02:02:54 2012 us=540410 Data Channel MTU parms [ L:1590 D:1450 EF:58 EB:135 ET:32 EL:0 AF:3/1 ]
Wed Feb 1 02:02:54 2012 us=544230 chroot to '/tmp/openvpn' and cd to '/' succeeded
Wed Feb 1 02:02:54 2012 us=545044 GID set to openvpn
Wed Feb 1 02:02:54 2012 us=545473 UID set to openvpn
Wed Feb 1 02:02:54 2012 us=545874 UDPv4 link local (bound): [undef]
Wed Feb 1 02:02:54 2012 us=546191 UDPv4 link remote: [undef]
Wed Feb 1 02:02:54 2012 us=546873 MULTI: multi_init called, r=256 v=256
Wed Feb 1 02:02:54 2012 us=549063 IFCONFIG POOL: base=192.168.2.101 size=20, ipv6=0
Wed Feb 1 02:02:54 2012 us=549991 Initialization Sequence Completed
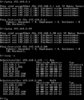
Wed Feb 1 02:05:20 2012 us=852555 MULTI: multi_create_instance called
Wed Feb 1 02:05:20 2012 us=853168 89.204.155.183:26658 Re-using SSL/TLS context
Wed Feb 1 02:05:20 2012 us=853715 89.204.155.183:26658 LZO compression initialized
Wed Feb 1 02:05:20 2012 us=856588 89.204.155.183:26658 Control Channel MTU parms [ L:1590 D:166 EF:66 EB:0 ET:0 EL:0 ]
Wed Feb 1 02:05:20 2012 us=857009 89.204.155.183:26658 Data Channel MTU parms [ L:1590 D:1450 EF:58 EB:135 ET:32 EL:0 AF:3/1 ]
Wed Feb 1 02:05:20 2012 us=858002 89.204.155.183:26658 UDPv4 READ [42] from [AF_INET]89.204.155.183:26658: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 pid=[ #1 ] [ ] pid=0 DATA len=0
Wed Feb 1 02:05:20 2012 us=858570 89.204.155.183:26658 TLS: Initial packet from [AF_INET]89.204.155.183:26658, sid=761bbf2a 0431702a
Wed Feb 1 02:05:20 2012 us=859364 89.204.155.183:26658 UDPv4 WRITE [54] to [AF_INET]89.204.155.183:26658: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 pid=[ #1 ] [ 0 ] pid=0 DATA len=0
Wed Feb 1 02:05:21 2012 us=250581 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #2 ] [ 0 ]
Wed Feb 1 02:05:21 2012 us=332682 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #3 ] [ ] pid=1 DATA len=100
Wed Feb 1 02:05:21 2012 us=333800 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #2 ] [ 1 ]
Wed Feb 1 02:05:21 2012 us=432570 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #4 ] [ ] pid=2 DATA len=100
Wed Feb 1 02:05:21 2012 us=433896 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #3 ] [ 2 ]
Wed Feb 1 02:05:21 2012 us=434881 89.204.155.183:26658 UDPv4 READ [52] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #5 ] [ ] pid=3 DATA len=10
Wed Feb 1 02:05:22 2012 us=393482 89.204.155.183:26658 UDPv4 WRITE [154] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #4 ] [ 3 ] pid=1 DATA len=100
Wed Feb 1 02:05:22 2012 us=394635 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #5 ] [ ] pid=2 DATA len=100
Wed Feb 1 02:05:22 2012 us=395764 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #6 ] [ ] pid=3 DATA len=100
Wed Feb 1 02:05:22 2012 us=396894 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #7 ] [ ] pid=4 DATA len=100
Wed Feb 1 02:05:22 2012 us=850534 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #6 ] [ 1 ]
Wed Feb 1 02:05:22 2012 us=851583 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #8 ] [ ] pid=5 DATA len=100
Wed Feb 1 02:05:22 2012 us=950568 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #7 ] [ 2 ]
Wed Feb 1 02:05:22 2012 us=951610 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #9 ] [ ] pid=6 DATA len=100
Wed Feb 1 02:05:22 2012 us=970502 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #8 ] [ 3 ]
Wed Feb 1 02:05:22 2012 us=971532 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #10 ] [ ] pid=7 DATA len=100
Wed Feb 1 02:05:23 2012 us=10441 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #9 ] [ 4 ]
Wed Feb 1 02:05:23 2012 us=11490 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #11 ] [ ] pid=8 DATA len=100
Wed Feb 1 02:05:23 2012 us=270613 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #10 ] [ 5 ]
Wed Feb 1 02:05:23 2012 us=271645 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #12 ] [ ] pid=9 DATA len=100
Wed Feb 1 02:05:23 2012 us=273697 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #11 ] [ 6 ]
Wed Feb 1 02:05:23 2012 us=274710 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #13 ] [ ] pid=10 DATA len=100
Wed Feb 1 02:05:23 2012 us=308060 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #12 ] [ 7 ]
Wed Feb 1 02:05:23 2012 us=309088 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #14 ] [ ] pid=11 DATA len=100
Wed Feb 1 02:05:23 2012 us=330488 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #13 ] [ 8 ]
Wed Feb 1 02:05:23 2012 us=331516 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #15 ] [ ] pid=12 DATA len=100
Wed Feb 1 02:05:23 2012 us=570444 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #14 ] [ 9 ]
Wed Feb 1 02:05:23 2012 us=571467 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #16 ] [ ] pid=13 DATA len=100
Wed Feb 1 02:05:23 2012 us=650516 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #15 ] [ 10 ]
Wed Feb 1 02:05:23 2012 us=651534 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #17 ] [ ] pid=14 DATA len=100
Wed Feb 1 02:05:23 2012 us=653544 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #16 ] [ 11 ]
Wed Feb 1 02:05:23 2012 us=654628 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #18 ] [ ] pid=15 DATA len=100
Wed Feb 1 02:05:23 2012 us=730609 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #17 ] [ 12 ]
Wed Feb 1 02:05:23 2012 us=731624 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #19 ] [ ] pid=16 DATA len=100
Wed Feb 1 02:05:23 2012 us=870525 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #18 ] [ 13 ]
Wed Feb 1 02:05:23 2012 us=871534 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #20 ] [ ] pid=17 DATA len=100
Wed Feb 1 02:05:23 2012 us=970552 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #19 ] [ 14 ]
Wed Feb 1 02:05:23 2012 us=971559 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #21 ] [ ] pid=18 DATA len=100
Wed Feb 1 02:05:24 2012 us=90614 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #20 ] [ 15 ]
Wed Feb 1 02:05:24 2012 us=91635 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #22 ] [ ] pid=19 DATA len=100
Wed Feb 1 02:05:24 2012 us=92736 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #21 ] [ 16 ]
Wed Feb 1 02:05:24 2012 us=93707 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #23 ] [ ] pid=20 DATA len=100
Wed Feb 1 02:05:24 2012 us=170858 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #22 ] [ 17 ]
Wed Feb 1 02:05:24 2012 us=171851 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #24 ] [ ] pid=21 DATA len=100
Wed Feb 1 02:05:24 2012 us=230491 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #23 ] [ 18 ]
Wed Feb 1 02:05:24 2012 us=231481 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #25 ] [ ] pid=22 DATA len=100
Wed Feb 1 02:05:24 2012 us=470457 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #24 ] [ 19 ]
Wed Feb 1 02:05:24 2012 us=471451 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #26 ] [ ] pid=23 DATA len=100
Wed Feb 1 02:05:24 2012 us=608333 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #25 ] [ 20 ]
Wed Feb 1 02:05:24 2012 us=609321 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #27 ] [ ] pid=24 DATA len=100
Wed Feb 1 02:05:24 2012 us=610304 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #26 ] [ 21 ]
Wed Feb 1 02:05:24 2012 us=611257 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #28 ] [ ] pid=25 DATA len=100
Wed Feb 1 02:05:24 2012 us=635435 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #27 ] [ 22 ]
Wed Feb 1 02:05:24 2012 us=636415 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #29 ] [ ] pid=26 DATA len=100
Wed Feb 1 02:05:24 2012 us=819285 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #28 ] [ 23 ]
Wed Feb 1 02:05:24 2012 us=820263 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #30 ] [ ] pid=27 DATA len=100
Wed Feb 1 02:05:25 2012 us=31871 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #29 ] [ 24 ]
Wed Feb 1 02:05:25 2012 us=32872 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #31 ] [ ] pid=28 DATA len=100
Wed Feb 1 02:05:25 2012 us=70383 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #30 ] [ 25 ]
Wed Feb 1 02:05:25 2012 us=71355 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #32 ] [ ] pid=29 DATA len=100
Wed Feb 1 02:05:25 2012 us=72571 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #31 ] [ 26 ]
Wed Feb 1 02:05:25 2012 us=73521 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #33 ] [ ] pid=30 DATA len=100
Wed Feb 1 02:05:25 2012 us=170411 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #32 ] [ 27 ]
Wed Feb 1 02:05:25 2012 us=171377 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #34 ] [ ] pid=31 DATA len=100
Wed Feb 1 02:05:25 2012 us=390426 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #33 ] [ 28 ]
Wed Feb 1 02:05:25 2012 us=391384 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #35 ] [ ] pid=32 DATA len=100
Wed Feb 1 02:05:25 2012 us=470489 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #34 ] [ 29 ]
Wed Feb 1 02:05:25 2012 us=471452 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #36 ] [ ] pid=33 DATA len=100
Wed Feb 1 02:05:25 2012 us=472842 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #35 ] [ 30 ]
Wed Feb 1 02:05:25 2012 us=473783 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #37 ] [ ] pid=34 DATA len=100
Wed Feb 1 02:05:25 2012 us=550559 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #36 ] [ 31 ]
Wed Feb 1 02:05:25 2012 us=551513 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #38 ] [ ] pid=35 DATA len=100
Wed Feb 1 02:05:25 2012 us=790528 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #37 ] [ 32 ]
Wed Feb 1 02:05:25 2012 us=791471 89.204.155.183:26658 UDPv4 WRITE [77] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #39 ] [ ] pid=36 DATA len=35
Wed Feb 1 02:05:25 2012 us=871097 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #38 ] [ 33 ]
Wed Feb 1 02:05:25 2012 us=872527 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #39 ] [ 34 ]
Wed Feb 1 02:05:25 2012 us=950447 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #40 ] [ 35 ]
Wed Feb 1 02:05:26 2012 us=333141 89.204.155.183:26658 UDPv4 READ [154] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #41 ] [ 36 ] pid=4 DATA len=100
Wed Feb 1 02:05:26 2012 us=334219 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #40 ] [ 4 ]
Wed Feb 1 02:05:26 2012 us=412418 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #42 ] [ ] pid=5 DATA len=100
Wed Feb 1 02:05:26 2012 us=413467 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #41 ] [ 5 ]
Wed Feb 1 02:05:26 2012 us=432599 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #43 ] [ ] pid=6 DATA len=100
Wed Feb 1 02:05:26 2012 us=433647 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #42 ] [ 6 ]
Wed Feb 1 02:05:26 2012 us=452586 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #44 ] [ ] pid=7 DATA len=100
Wed Feb 1 02:05:26 2012 us=453638 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #43 ] [ 7 ]
Wed Feb 1 02:05:26 2012 us=749465 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #45 ] [ ] pid=8 DATA len=100
Wed Feb 1 02:05:26 2012 us=750516 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #44 ] [ 8 ]
Wed Feb 1 02:05:26 2012 us=953355 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #46 ] [ ] pid=9 DATA len=100
Wed Feb 1 02:05:26 2012 us=954683 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #45 ] [ 9 ]
Wed Feb 1 02:05:26 2012 us=955671 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #47 ] [ ] pid=10 DATA len=100
Wed Feb 1 02:05:26 2012 us=956697 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #46 ] [ 10 ]
Wed Feb 1 02:05:26 2012 us=957946 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #48 ] [ ] pid=11 DATA len=100
Wed Feb 1 02:05:26 2012 us=958993 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #47 ] [ 11 ]
Wed Feb 1 02:05:27 2012 us=221796 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #49 ] [ ] pid=12 DATA len=100
Wed Feb 1 02:05:27 2012 us=222862 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #48 ] [ 12 ]
Wed Feb 1 02:05:27 2012 us=275365 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #50 ] [ ] pid=13 DATA len=100
Wed Feb 1 02:05:27 2012 us=276418 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #49 ] [ 13 ]
Wed Feb 1 02:05:27 2012 us=352323 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #51 ] [ ] pid=14 DATA len=100
Wed Feb 1 02:05:27 2012 us=353380 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #50 ] [ 14 ]
Wed Feb 1 02:05:27 2012 us=411972 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #52 ] [ ] pid=15 DATA len=100
Wed Feb 1 02:05:27 2012 us=413024 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #51 ] [ 15 ]
Wed Feb 1 02:05:27 2012 us=649963 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #53 ] [ ] pid=16 DATA len=100
Wed Feb 1 02:05:27 2012 us=651016 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #52 ] [ 16 ]
Wed Feb 1 02:05:27 2012 us=712283 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #54 ] [ ] pid=17 DATA len=100
Wed Feb 1 02:05:27 2012 us=713338 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #53 ] [ 17 ]
Wed Feb 1 02:05:27 2012 us=729527 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #55 ] [ ] pid=18 DATA len=100
Wed Feb 1 02:05:27 2012 us=730576 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #54 ] [ 18 ]
Wed Feb 1 02:05:27 2012 us=772396 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #56 ] [ ] pid=19 DATA len=100
Wed Feb 1 02:05:27 2012 us=773446 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #55 ] [ 19 ]
Wed Feb 1 02:05:28 2012 us=69557 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #57 ] [ ] pid=20 DATA len=100
Wed Feb 1 02:05:28 2012 us=70621 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #56 ] [ 20 ]
Wed Feb 1 02:05:28 2012 us=149589 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #58 ] [ ] pid=21 DATA len=100
Wed Feb 1 02:05:28 2012 us=150721 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #57 ] [ 21 ]
Wed Feb 1 02:05:28 2012 us=172524 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #59 ] [ ] pid=22 DATA len=100
Wed Feb 1 02:05:28 2012 us=173574 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #58 ] [ 22 ]
Wed Feb 1 02:05:28 2012 us=212426 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #60 ] [ ] pid=23 DATA len=100
Wed Feb 1 02:05:28 2012 us=213478 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #59 ] [ 23 ]
Wed Feb 1 02:05:28 2012 us=713052 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #61 ] [ ] pid=24 DATA len=100
Wed Feb 1 02:05:28 2012 us=714103 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #60 ] [ 24 ]
Wed Feb 1 02:05:28 2012 us=716410 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #62 ] [ ] pid=25 DATA len=100
Wed Feb 1 02:05:28 2012 us=717726 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #61 ] [ 25 ]
Wed Feb 1 02:05:28 2012 us=720214 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #63 ] [ ] pid=26 DATA len=100
Wed Feb 1 02:05:28 2012 us=721251 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #62 ] [ 26 ]
Wed Feb 1 02:05:28 2012 us=723384 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #64 ] [ ] pid=27 DATA len=100
Wed Feb 1 02:05:28 2012 us=724417 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #63 ] [ 27 ]
Wed Feb 1 02:05:29 2012 us=229978 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #65 ] [ ] pid=28 DATA len=100
Wed Feb 1 02:05:29 2012 us=236721 89.204.155.183:26658 VERIFY OK: depth=1,
Wed Feb 1 02:05:29 2012 us=244618 89.204.155.183:26658 VERIFY OK: depth=0,
Wed Feb 1 02:05:29 2012 us=245550 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #64 ] [ 28 ]
Wed Feb 1 02:05:29 2012 us=336779 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #66 ] [ ] pid=29 DATA len=100
Wed Feb 1 02:05:29 2012 us=339016 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #65 ] [ 29 ]
Wed Feb 1 02:05:29 2012 us=372778 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #67 ] [ ] pid=30 DATA len=100
Wed Feb 1 02:05:29 2012 us=373824 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #66 ] [ 30 ]
Wed Feb 1 02:05:29 2012 us=432874 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #68 ] [ ] pid=31 DATA len=100
Wed Feb 1 02:05:30 2012 us=159468 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #67 ] [ 31 ]
Wed Feb 1 02:05:30 2012 us=160481 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #69 ] [ ] pid=32 DATA len=100
Wed Feb 1 02:05:30 2012 us=161526 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #68 ] [ 32 ]
Wed Feb 1 02:05:30 2012 us=162509 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #70 ] [ ] pid=33 DATA len=100
Wed Feb 1 02:05:30 2012 us=163538 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #69 ] [ 33 ]
Wed Feb 1 02:05:30 2012 us=164609 89.204.155.183:26658 UDPv4 READ [127] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #71 ] [ ] pid=34 DATA len=85
Wed Feb 1 02:05:30 2012 us=176545 89.204.155.183:26658 UDPv4 WRITE [154] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #70 ] [ 34 ] pid=37 DATA len=100
Wed Feb 1 02:05:30 2012 us=178283 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #71 ] [ ] pid=38 DATA len=100
Wed Feb 1 02:05:30 2012 us=179290 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #72 ] [ ] pid=39 DATA len=100
Wed Feb 1 02:05:30 2012 us=180264 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #73 ] [ ] pid=40 DATA len=100
Wed Feb 1 02:05:30 2012 us=530056 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #72 ] [ 37 ]
Wed Feb 1 02:05:30 2012 us=530955 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #74 ] [ ] pid=41 DATA len=100
Wed Feb 1 02:05:30 2012 us=610370 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #73 ] [ 38 ]
Wed Feb 1 02:05:30 2012 us=611269 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #75 ] [ ] pid=42 DATA len=100
Wed Feb 1 02:05:30 2012 us=613315 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #74 ] [ 39 ]
Wed Feb 1 02:05:30 2012 us=614186 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #76 ] [ ] pid=43 DATA len=100
Wed Feb 1 02:05:30 2012 us=690435 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #75 ] [ 40 ]
Wed Feb 1 02:05:30 2012 us=691331 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #77 ] [ ] pid=44 DATA len=100
Wed Feb 1 02:05:30 2012 us=830382 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #76 ] [ 41 ]
Wed Feb 1 02:05:30 2012 us=831268 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #78 ] [ ] pid=45 DATA len=100
Wed Feb 1 02:05:30 2012 us=930409 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #77 ] [ 42 ]
Wed Feb 1 02:05:30 2012 us=931294 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #79 ] [ ] pid=46 DATA len=100
Wed Feb 1 02:05:31 2012 us=50396 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #78 ] [ 43 ]
Wed Feb 1 02:05:31 2012 us=51295 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #80 ] [ ] pid=47 DATA len=100
Wed Feb 1 02:05:31 2012 us=52296 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #79 ] [ 44 ]
Wed Feb 1 02:05:31 2012 us=53149 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #81 ] [ ] pid=48 DATA len=100
Wed Feb 1 02:05:31 2012 us=130479 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #80 ] [ 45 ]
Wed Feb 1 02:05:31 2012 us=131354 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #82 ] [ ] pid=49 DATA len=100
Wed Feb 1 02:05:31 2012 us=190321 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #81 ] [ 46 ]
Wed Feb 1 02:05:31 2012 us=191194 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #83 ] [ ] pid=50 DATA len=100
Wed Feb 1 02:05:31 2012 us=440812 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #82 ] [ 47 ]
Wed Feb 1 02:05:31 2012 us=441764 89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #84 ] [ ] pid=51 DATA len=100
Wed Feb 1 02:05:31 2012 us=579342 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #83 ] [ 48 ]
Wed Feb 1 02:05:31 2012 us=580340 89.204.155.183:26658 UDPv4 WRITE [56] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #85 ] [ ] pid=52 DATA len=14
Wed Feb 1 02:05:31 2012 us=581210 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #84 ] [ 49 ]
Wed Feb 1 02:05:31 2012 us=675349 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #85 ] [ 50 ]
Wed Feb 1 02:05:31 2012 us=810446 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #86 ] [ 51 ]
Wed Feb 1 02:05:32 2012 us=109862 89.204.155.183:26658 UDPv4 READ [154] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #87 ] [ 52 ] pid=35 DATA len=100
Wed Feb 1 02:05:32 2012 us=110997 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #86 ] [ 35 ]
Wed Feb 1 02:05:32 2012 us=189910 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #88 ] [ ] pid=36 DATA len=100
Wed Feb 1 02:05:32 2012 us=190810 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #87 ] [ 36 ]
Wed Feb 1 02:05:32 2012 us=212573 89.204.155.183:26658 UDPv4 READ [142] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #89 ] [ ] pid=37 DATA len=100
Wed Feb 1 02:05:32 2012 us=213472 89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #88 ] [ 37 ]
Wed Feb 1 02:05:32 2012 us=250489 89.204.155.183:26658 UDPv4 READ [72] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #90 ] [ ] pid=38 DATA len=30
Wed Feb 1 02:05:32 2012 us=253817 89.204.155.183:26658 Data Channel Encrypt: Cipher 'AES-256-CBC' initialized with 256 bit key
Wed Feb 1 02:05:32 2012 us=254243 89.204.155.183:26658 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 1 02:05:32 2012 us=254638 89.204.155.183:26658 Data Channel Decrypt: Cipher 'AES-256-CBC' initialized with 256 bit key
Wed Feb 1 02:05:32 2012 us=255030 89.204.155.183:26658 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 1 02:05:32 2012 us=256365 89.204.155.183:26658 UDPv4 WRITE [154] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #89 ] [ 38 ] pid=53 DATA len=100
Wed Feb 1 02:05:32 2012 us=257311 89.204.155.183:26658 UDPv4 WRITE [96] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #90 ] [ ] pid=54 DATA len=54
Wed Feb 1 02:05:32 2012 us=790687 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #91 ] [ 53 ]
Wed Feb 1 02:05:32 2012 us=792477 89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #92 ] [ 54 ]
Wed Feb 1 02:05:32 2012 us=793092 89.204.155.183:26658 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA
Wed Feb 1 02:05:32 2012 us=793597 89.204.155.183:26658 [client01] Peer Connection Initiated with [AF_INET]89.204.155.183:26658
Wed Feb 1 02:05:32 2012 us=794315 client01/89.204.155.183:26658 MULTI_sva: pool returned IPv4=192.168.2.101, IPv6=444d:4100:6887:4700:c03d:4200:e086:4700
Wed Feb 1 02:05:33 2012 us=553377 client01/89.204.155.183:26658 UDPv4 WRITE [117] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:34 2012 us=552939 client01/89.204.155.183:26658 UDPv4 WRITE [117] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:35 2012 us=352386 client01/89.204.155.183:26658 UDPv4 READ [132] from [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #93 ] [ ] pid=39 DATA len=90
Wed Feb 1 02:05:35 2012 us=353431 client01/89.204.155.183:26658 PUSH: Received control message: 'PUSH_REQUEST'
Wed Feb 1 02:05:35 2012 us=353850 client01/89.204.155.183:26658 send_push_reply(): safe_cap=960
Wed Feb 1 02:05:35 2012 us=354729 client01/89.204.155.183:26658 SENT CONTROL [client01]: 'PUSH_REPLY,route-gateway 192.168.2.100,route 192.168.2.0 255.255.255.0,route 192.168.2.0 255.255.255.0,redirect-gateway,ping 10,ping-restart 120,ifconfig 192.168.2.101 255.255.255.0' (status=1)
Wed Feb 1 02:05:35 2012 us=355293 client01/89.204.155.183:26658 UDPv4 WRITE [50] to [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #91 ] [ 39 ]
Wed Feb 1 02:05:35 2012 us=356226 client01/89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #92 ] [ ] pid=55 DATA len=100
Wed Feb 1 02:05:35 2012 us=357163 client01/89.204.155.183:26658 UDPv4 WRITE [142] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #93 ] [ ] pid=56 DATA len=100
Wed Feb 1 02:05:35 2012 us=358375 client01/89.204.155.183:26658 UDPv4 WRITE [92] to [AF_INET]89.204.155.183:26658: P_CONTROL_V1 kid=0 pid=[ #94 ] [ ] pid=57 DATA len=50
Wed Feb 1 02:05:35 2012 us=552923 client01/89.204.155.183:26658 UDPv4 WRITE [117] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:35 2012 us=650454 client01/89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #94 ] [ 55 ]
Wed Feb 1 02:05:35 2012 us=727324 client01/89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #95 ] [ 56 ]
Wed Feb 1 02:05:35 2012 us=986326 client01/89.204.155.183:26658 UDPv4 READ [50] from [AF_INET]89.204.155.183:26658: P_ACK_V1 kid=0 pid=[ #96 ] [ 57 ]
Wed Feb 1 02:05:35 2012 us=987393 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:35 2012 us=988540 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:36 2012 us=24520 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:36 2012 us=96282 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:36 2012 us=102176 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:36 2012 us=133204 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:36 2012 us=162799 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:36 2012 us=240562 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:36 2012 us=241624 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:36 2012 us=242661 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:36 2012 us=432429 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:36 2012 us=435284 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:36 2012 us=441284 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:36 2012 us=444647 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:36 2012 us=447699 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:36 2012 us=712805 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:36 2012 us=716665 client01/89.204.155.183:26658 UDPv4 READ [181] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=180
Wed Feb 1 02:05:36 2012 us=741238 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:36 2012 us=852108 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:37 2012 us=332306 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:37 2012 us=351568 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:37 2012 us=353101 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:37 2012 us=355756 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:37 2012 us=359300 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:37 2012 us=362735 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:37 2012 us=424551 client01/89.204.155.183:26658 UDPv4 READ [741] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=740
Wed Feb 1 02:05:37 2012 us=525093 client01/89.204.155.183:26658 UDPv4 READ [773] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=772
Wed Feb 1 02:05:37 2012 us=886029 client01/89.204.155.183:26658 UDPv4 READ [773] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=772
Wed Feb 1 02:05:37 2012 us=898560 client01/89.204.155.183:26658 UDPv4 READ [741] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=740
Wed Feb 1 02:05:37 2012 us=899756 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:37 2012 us=901785 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:37 2012 us=904233 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:38 2012 us=213135 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:38 2012 us=213933 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:38 2012 us=214830 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:38 2012 us=215740 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:38 2012 us=216656 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:38 2012 us=252722 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:38 2012 us=253801 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:38 2012 us=254588 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:38 2012 us=255484 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:38 2012 us=279812 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:38 2012 us=333391 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:38 2012 us=364033 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:38 2012 us=394212 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:38 2012 us=432260 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:38 2012 us=435353 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:38 2012 us=439206 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:39 2012 us=69909 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:39 2012 us=109797 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:39 2012 us=151473 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:39 2012 us=169048 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:39 2012 us=189034 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:39 2012 us=208325 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:39 2012 us=249250 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:39 2012 us=289881 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:39 2012 us=309826 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:39 2012 us=891294 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:39 2012 us=895201 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:39 2012 us=899038 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:39 2012 us=902371 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:40 2012 us=34940 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:40 2012 us=109341 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:40 2012 us=511265 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:40 2012 us=512052 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:40 2012 us=518675 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:40 2012 us=543470 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:40 2012 us=544404 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:40 2012 us=545286 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:40 2012 us=546318 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:40 2012 us=547087 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:40 2012 us=548126 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:40 2012 us=610052 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:40 2012 us=692117 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:40 2012 us=852327 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:40 2012 us=853558 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:40 2012 us=871845 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:40 2012 us=892307 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:40 2012 us=912249 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:40 2012 us=928940 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:41 2012 us=112026 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:41 2012 us=113243 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:41 2012 us=224645 client01/89.204.155.183:26658 UDPv4 READ [741] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=740
Wed Feb 1 02:05:41 2012 us=325682 client01/89.204.155.183:26658 UDPv4 READ [773] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=772
Wed Feb 1 02:05:41 2012 us=353286 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:41 2012 us=764971 client01/89.204.155.183:26658 UDPv4 READ [773] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=772
Wed Feb 1 02:05:41 2012 us=785625 client01/89.204.155.183:26658 UDPv4 READ [741] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=740
Wed Feb 1 02:05:41 2012 us=786832 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:41 2012 us=789370 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:41 2012 us=792294 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:41 2012 us=796175 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:41 2012 us=798134 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:41 2012 us=802416 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:41 2012 us=805780 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:41 2012 us=809311 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:42 2012 us=498061 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:42 2012 us=502569 client01/89.204.155.183:26658 UDPv4 READ [293] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=292
Wed Feb 1 02:05:42 2012 us=540020 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:42 2012 us=541019 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:42 2012 us=541775 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:42 2012 us=542964 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:42 2012 us=544478 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:42 2012 us=545308 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:42 2012 us=581648 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:42 2012 us=583026 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:42 2012 us=584414 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:42 2012 us=585405 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:42 2012 us=992453 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:43 2012 us=211445 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:43 2012 us=628604 client01/89.204.155.183:26658 UDPv4 WRITE [85] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:43 2012 us=832323 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:43 2012 us=851775 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:43 2012 us=944103 client01/89.204.155.183:26658 UDPv4 WRITE [117] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:44 2012 us=71793 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:44 2012 us=95307 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:44 2012 us=97072 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:44 2012 us=98156 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:44 2012 us=119627 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:44 2012 us=140150 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:44 2012 us=141796 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:44 2012 us=142710 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:44 2012 us=372365 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:44 2012 us=411271 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:44 2012 us=455037 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:44 2012 us=471385 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:44 2012 us=512294 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:44 2012 us=531777 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:44 2012 us=551221 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:44 2012 us=572428 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:44 2012 us=591879 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:44 2012 us=611348 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:44 2012 us=943724 client01/89.204.155.183:26658 UDPv4 WRITE [117] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:45 2012 us=2684 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:45 2012 us=189688 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:45 2012 us=191212 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:45 2012 us=191985 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:45 2012 us=469236 client01/89.204.155.183:26658 UDPv4 READ [1109] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1108
Wed Feb 1 02:05:45 2012 us=488119 client01/89.204.155.183:26658 UDPv4 READ [1077] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=1076
Wed Feb 1 02:05:45 2012 us=489490 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:45 2012 us=490268 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:45 2012 us=491787 client01/89.204.155.183:26658 UDPv4 READ [101] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=100
Wed Feb 1 02:05:45 2012 us=495298 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:45 2012 us=511846 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:45 2012 us=612398 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:45 2012 us=655284 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:45 2012 us=671240 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:45 2012 us=713911 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:45 2012 us=753827 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:45 2012 us=773798 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:45 2012 us=813937 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:45 2012 us=873320 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:45 2012 us=914453 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:45 2012 us=943704 client01/89.204.155.183:26658 UDPv4 WRITE [117] to [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:45 2012 us=953879 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:45 2012 us=991792 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:46 2012 us=111995 client01/89.204.155.183:26658 UDPv4 READ [117] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=116
Wed Feb 1 02:05:46 2012 us=492915 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:46 2012 us=510972 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:46 2012 us=555291 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:46 2012 us=689775 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:46 2012 us=768343 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:47 2012 us=472006 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:47 2012 us=691766 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:48 2012 us=274269 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:48 2012 us=389283 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:48 2012 us=394200 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:48 2012 us=452349 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:48 2012 us=533905 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:48 2012 us=538999 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:48 2012 us=542245 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:48 2012 us=545195 client01/89.204.155.183:26658 UDPv4 READ [133] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=132
Wed Feb 1 02:05:48 2012 us=550955 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:48 2012 us=611742 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:49 2012 us=318259 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:49 2012 us=319326 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:49 2012 us=320553 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:49 2012 us=321484 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:49 2012 us=322466 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:49 2012 us=359091 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:49 2012 us=912849 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:49 2012 us=916199 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:49 2012 us=919763 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:49 2012 us=921607 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:50 2012 us=192306 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:50 2012 us=193616 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:50 2012 us=489871 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:50 2012 us=628313 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:51 2012 us=211811 client01/89.204.155.183:26658 UDPv4 READ [277] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=276
Wed Feb 1 02:05:51 2012 us=230264 client01/89.204.155.183:26658 UDPv4 READ [213] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=212
Wed Feb 1 02:05:51 2012 us=294990 client01/89.204.155.183:26658 UDPv4 READ [229] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=228
Wed Feb 1 02:05:51 2012 us=312275 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:51 2012 us=559633 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:51 2012 us=854880 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:52 2012 us=152672 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:52 2012 us=312316 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:52 2012 us=314655 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:52 2012 us=949207 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:53 2012 us=32731 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164
Wed Feb 1 02:05:53 2012 us=130775 client01/89.204.155.183:26658 UDPv4 READ [85] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=84
Wed Feb 1 02:05:53 2012 us=695205 client01/89.204.155.183:26658 UDPv4 READ [149] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=148
Wed Feb 1 02:05:53 2012 us=764123 client01/89.204.155.183:26658 UDPv4 READ [165] from [AF_INET]89.204.155.183:26658: P_DATA_V1 kid=0 DATA len=164