Hallo Community!
Da ich bei Google Recherchen zu VPN via FritzBox des öfteren auf Postings aus diesem Forum gestoßen bin, dachte ich ich melde mich hier mal an um mit meinem aktuellen Problem evtl. fachkundige Hilfestellung zu bekommen
.
Ich möchte einen VPN Tunnel zwischen einer FritzBox 3490 (OS 7.12) zu einem LANCOM 1781VA (OS 10.32.0157RU5) etablieren.
FB vpn.cfg:
Da ich nicht genau wusste, welche Strategien die Box zur Verfügung stellt, habe ich mit mal das aktuelle Firmware Image zerlegt und einen Blick in die ipsec.cfg geworfen. Ich habe mich basierend darauf dann für folgende Strategien entschieden:
phase1ss:
phase2ss:
Diese müssten meinem Verständnis nach mit den getroffenen Einstellungen im LANCOM kompatibel sein:
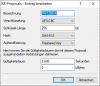
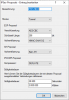
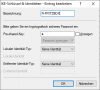
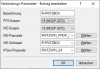
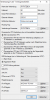
[Edit Novize: Bilder gemäß der Forenregeln auf Vorschau geschrumpft]
Leider bekomme ich so keine Verbindung zustande.
Im LANmonitor bekomme ich folgenden Fehler angezeigt:
Zeitüberschreitung während IKE- oder IPSec-Verhandlung (Aktiver Verbindungsaufbau) [0x1106]
In der Fritzbox lediglich einmal:
VPN-Fehler: R-LANCOM, IKE Error 0x2026
direkt nach übernahme der Config. Für mich leider nicht wirklich aussagekräftig.
Also erweitertes Supportlog von der Fritzbox gezogen und einen Blick rein geworfen.
Ausgehend von FB:
Eingehend von LANCOM:
Daraus entnehme ich, dass es in Phase 1 schon scheitert. Allerdings erkenne ich nicht, woran. Ebenfalls erkenne ich, dass vom LANCOM laufend Anfragen zum Aufbau des Tunnels eingehen - diese verlaufen sich in der Fritzbox dann im Sand. Ich erkenne leider nicht, weshalb.
Nun komme ich nicht mehr weiter. Ich könnte noch einen Trace im LANCOM laufen lassen - allerdings sind die Trace-Einstellungen dann doch etwas zu komplex. ich weiß nicht, welche davon zum Debuggen der VPN essentiell und welche überflüssig sind.
Freue mich auf Rückmeldungen und Lösungsvorschläge!
Da ich bei Google Recherchen zu VPN via FritzBox des öfteren auf Postings aus diesem Forum gestoßen bin, dachte ich ich melde mich hier mal an um mit meinem aktuellen Problem evtl. fachkundige Hilfestellung zu bekommen
.
Ich möchte einen VPN Tunnel zwischen einer FritzBox 3490 (OS 7.12) zu einem LANCOM 1781VA (OS 10.32.0157RU5) etablieren.
FB vpn.cfg:
Code:
vpncfg {
connections {
enabled = yes;
editable = no;
conn_type = conntype_lan;
name = "R-LANCOM";
always_renew = yes;
reject_not_encrypted = no;
dont_filter_netbios = yes;
localip = 0.0.0.0;
local_virtualip = 0.0.0.0;
remotehostname = "lancom.host.name";
keepalive_ip = 192.168.2.1;
remotevirtualip = 0.0.0.0;
mode = phase1_mode_aggressive;
phase1ss = "dh15/aes/sha";
keytype = connkeytype_pre_shared;
key = "%geheim%";
cert_do_server_auth = no;
use_nat_t = yes;
use_xauth = no;
use_cfgmode = no;
phase2localid {
ipnet {
ipaddr = 192.168.1.0;
mask = 255.255.255.0;
}
}
phase2remoteid {
ipnet {
ipaddr = 192.168.2.0;
mask = 255.255.255.0;
}
}
phase2ss = "LT8h/esp-all-all/ah-none/comp-all/pfs";
accesslist = "permit ip any 192.168.2.0 255.255.255.0";
}
ike_forward_rules = "udp 0.0.0.0:500 0.0.0.0:500",
"udp 0.0.0.0:4500 0.0.0.0:4500";
}
// EOFDa ich nicht genau wusste, welche Strategien die Box zur Verfügung stellt, habe ich mit mal das aktuelle Firmware Image zerlegt und einen Blick in die ipsec.cfg geworfen. Ich habe mich basierend darauf dann für folgende Strategien entschieden:
phase1ss:
Code:
{
name = "dh15/aes/sha";
comment = "dh_group_modp15";
dhgroup = dh_group_modp15;
life_dur_sec = 1h;
life_dur_kb = 0;
accept_all_dh_groups = no;
proposals {
hash = ike_sha2_512;
enc {
type = ike_aes;
keylength = 256;
}
}{
hash = ike_sha;
enc {
type = ike_aes;
keylength = 256;
}
}{
hash = ike_sha;
enc {
type = ike_aes;
keylength = 192;
}
} {
hash = ike_sha;
enc {
type = ike_aes;
keylength = 0;
}
}
}phase2ss:
Code:
{
name = "LT8h/esp-all-all/ah-none/comp-all/pfs";
comment = "Alle Algorithmen, ohne AH, mit PFS";
pfs = yes;
life_dur_sec = 8h;
life_dur_kb = 0;
proposals {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = hmac_sha2_512;
}
}{
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = hmac_sha2_512;
}
}{
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = hmac_sha2_512;
}
}{
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = sha;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = sha;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = sha;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 192;
hash = sha;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 192;
hash = sha;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 192;
hash = sha;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_3des;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_3des;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_3des;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_des;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_des;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_des;
enc_key_length = 0;
hash = sha;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = md5;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = md5;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 256;
hash = md5;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 192;
hash = md5;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 192;
hash = md5;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 192;
hash = md5;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_aes;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_3des;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_3des;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_3des;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_lzjh;
ah = ah_none;
esp {
typ = esp_des;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_deflate;
ah = ah_none;
esp {
typ = esp_des;
enc_key_length = 0;
hash = md5;
}
} {
comp = comp_none;
ah = ah_none;
esp {
typ = esp_des;
enc_key_length = 0;
hash = md5;
}
}
}Diese müssten meinem Verständnis nach mit den getroffenen Einstellungen im LANCOM kompatibel sein:





[Edit Novize: Bilder gemäß der Forenregeln auf Vorschau geschrumpft]
Leider bekomme ich so keine Verbindung zustande.
Im LANmonitor bekomme ich folgenden Fehler angezeigt:
Zeitüberschreitung während IKE- oder IPSec-Verhandlung (Aktiver Verbindungsaufbau) [0x1106]
In der Fritzbox lediglich einmal:
VPN-Fehler: R-LANCOM, IKE Error 0x2026
direkt nach übernahme der Config. Für mich leider nicht wirklich aussagekräftig.
Also erweitertes Supportlog von der Fritzbox gezogen und einen Blick rein geworfen.
Ausgehend von FB:
Code:
2020-02-08 22:08:38 avmike:< add(appl=dsld,cname=%REMOTELANCOM%,localip=%LOCALIP%, remoteip=255.255.255.255, p1ss=dh15/aes/sha, p2ss=LT8h/esp-all-all/ah-none/comp-all/pfs p1mode=4 keepalive_ip=0.0.0.0 flags=0x48001 tunnel no_xauth no_cfgmode nat_t no_certsrv_server_auth)
2020-02-08 22:08:38 avmike:new neighbour %REMOTELANCOM%: nat_t
2020-02-08 22:08:38 avmike:< create_sa(appl=dsld,cname=%REMOTELANCOM%)
2020-02-08 22:08:38 avmike:%REMOTELANCOM%: Phase 1 starting
2020-02-08 22:08:41 avmike:>>> aggressive mode [%REMOTEIP%] %REMOTELANCOM%: V1.0 720 IC 41a1e2b7c186504 RC 00000000 0000 SA flags=
2020-02-08 22:08:42 avmike:%REMOTELANCOM%: Warning: source changed from 0.0.0.0:500 to %REMOTEIP%:500
2020-02-08 22:08:42 avmike:<<< infomode[%REMOTEIP%] %REMOTELANCOM%: V1.0 40 IC 41a1e2b7c186504 RC e9a3761b13aadd54 0000 NOTIFICATION flags=
2020-02-08 22:08:42 avmike:%REMOTELANCOM%: Phase 1 failed (initiator): IKE-Error 0x2026
2020-02-08 22:08:42 avmike:< cb_sa_create_failed(name=%REMOTELANCOM%,reason=IKE-Error 0x2026)Eingehend von LANCOM:
Code:
2020-02-08 22:09:16 avmike:> user_query(ipaddr=%REMOTEIP%)
2020-02-08 22:09:16 avmike:%REMOTEIP%: aggrmode: init aggr-exchange: user request send ID_IPV4_ADDR :%REMOTEIP%
2020-02-08 22:09:23 avmike:<<< aggressive mode[%REMOTEIP%] ???: V1.0 616 IC ba20c19ca29b3ff2 RC 00000000 0000 SA flags=
2020-02-08 22:09:32 avmike:<<< aggressive mode[%REMOTEIP%] ???: V1.0 616 IC ba20c19ca29b3ff2 RC 00000000 0000 SA flags=
2020-02-08 22:09:43 avmike:<<< aggressive mode[%REMOTEIP%] ???: V1.0 616 IC ba20c19ca29b3ff2 RC 00000000 0000 SA flags=
2020-02-08 22:10:10 avmike:<<< aggressive mode[%REMOTEIP%] ???: V1.0 616 IC 8ed3197e5e5dcef5 RC 00000000 0000 SA flags=
2020-02-08 22:10:10 avmike:unknown receive VENDOR ID Payload: NAT-T RFC 3947
2020-02-08 22:10:10 avmike:unknown receive VENDOR ID Payload: XAUTH
2020-02-08 22:10:10 avmike:unknown receive VENDOR ID Payload: DPD
[Wiederholend]Daraus entnehme ich, dass es in Phase 1 schon scheitert. Allerdings erkenne ich nicht, woran. Ebenfalls erkenne ich, dass vom LANCOM laufend Anfragen zum Aufbau des Tunnels eingehen - diese verlaufen sich in der Fritzbox dann im Sand. Ich erkenne leider nicht, weshalb.
Nun komme ich nicht mehr weiter. Ich könnte noch einen Trace im LANCOM laufen lassen - allerdings sind die Trace-Einstellungen dann doch etwas zu komplex. ich weiß nicht, welche davon zum Debuggen der VPN essentiell und welche überflüssig sind.
Freue mich auf Rückmeldungen und Lösungsvorschläge!